Penetration testing for WordPress websites is a crucial step in ensuring WordPress security. While Hollywood often simplifies hacking as an overnight feat, the real process of WordPress penetration involves a lot of trial, error, and patience. However, this should not discourage you, as mastering WordPress penetration testing can save your website from potential attacks.
This guide will take you through the steps of setting up a secure testing environment and using the most common tools for penetration testing on WordPress websites.

The Role of Penetration Testing in WordPress Security
The security of your WordPress websites plays a key role in their overall health and performance. WordPress security risks, such as plugin vulnerabilities and configuration flaws, can put your site at risk of hacking. Penetration testing helps identify these vulnerabilities, allowing you to fix them before bad actors exploit them.
This process, however, requires extensive technical knowledge of various security tools and how they integrate with WordPress websites. In this guide, we’ll walk you through some industry-standard tools like Kali Linux, WPScan, and Metasploit, which are widely used for WordPress penetration testing.
Step 1: Setting up Your Environment
Before diving into the technicalities, it’s important to set up a secure environment for penetration testing. A reliable tool for this is Kali Linux, a specialized OS designed for security testing.
What is Kali Linux?
Kali Linux is a popular security-focused Linux distribution widely used by penetration testers. With a variety of pre-installed security tools, it’s ideal for scanning WordPress websites for vulnerabilities. You can run Kali Linux in a Virtual Machine (VM) en`vironment, such as VMWare Workstation or Oracle’s VirtualBox, making it easy to test without affecting your live website.

Setting up the Virtual Environment
To set up, you’ll need to:
- Download VMWare Workstation or VirtualBox
- Install Kali Linux and a staging WordPress website (using Ubuntu as an example) in two separate VMs.
- Mimic your live site setup as closely as possible to ensure accurate vulnerability findings.
Common WordPress Vulnerabilities
To set up, you’ll need to:
- Download VMWare Workstation or VirtualBox
- Install Kali Linux and a staging WordPress website (using Ubuntu as an example) in two separate VMs.
- Mimic your live site setup as closely as possible to ensure accurate vulnerability findings.
Stage 2: Reconnaissance (aka Information Gathering)
The next step in WordPress penetration testing is gathering information about your target site. This phase is critical because it helps you identify potential weak spots on your WordPress website.
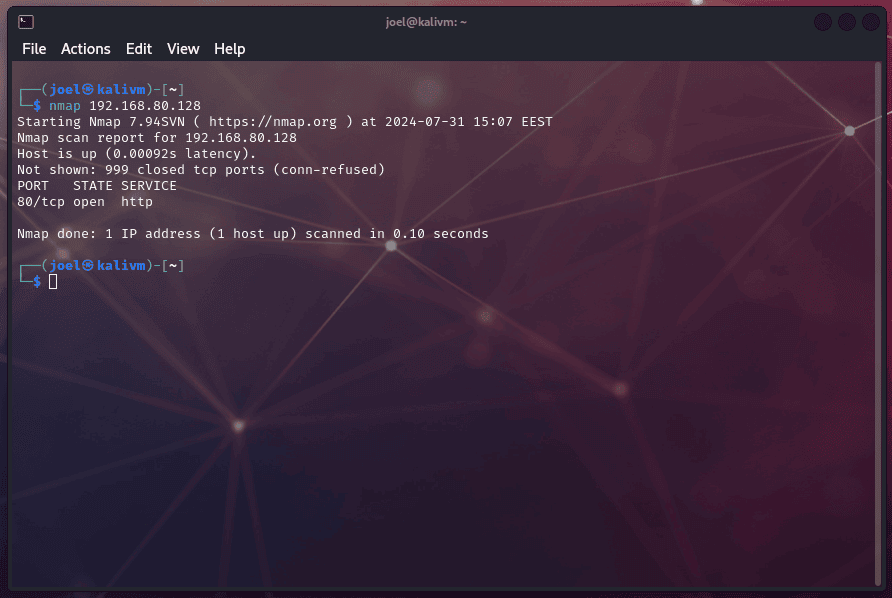
Technical Reconnaissance Tools
Some common tools to use during reconnaissance are:
- Nmap and Zenmap: These tools help you identify open ports and running services on your WordPress server.
- WPScan: A dedicated vulnerability scanner for WordPress websites. It identifies weak points in your plugin dashboard, themes, and core WordPress installation.
- Nikto: Another scanner that identifies vulnerabilities at the server level, including on WordPress websites.
Stage 3: Vulnerability Exploitation
After identifying vulnerabilities, the next step is to exploit them. Tools like Burp Suite and Metasploit come into play here, allowing you to simulate attacks and see how well your WordPress website holds up against potential breaches.
- Burp Suite is widely used for web app security testing and allows you to intercept and modify HTTP requests to exploit vulnerabilities.
- Metasploit is a powerful framework used for running exploit modules, which you can apply directly to vulnerabilities found in WordPress websites.
How to Minimize the Risk of Being Hacked
Securing your WordPress website after conducting a penetration test is just as important as finding vulnerabilities. Here are some key tips to reduce the risk of attacks:
1. Update Software Regularly
Keep all software up-to-date, including WordPress core, plugins, and themes. Vulnerabilities often target outdated versions, so updating your software helps protect against known threats.
2. Follow WordPress Security Best Practices
Implement strong login security by enforcing 2FA, using strong password policies, and limiting login attempts. This reduces the risk of brute-force attacks.
3. Harden Systems
System hardening involves making your WordPress website less susceptible to attacks by tweaking configurations. This can include securing PHP settings, hardening your plugin dashboard, and applying strong database protections.
Conclusion
Penetration testing for WordPress websites is a vital process for maintaining WordPress security. Using tools like Kali Linux, WPScan, Metasploit, and others will help you uncover vulnerabilities that may otherwise go unnoticed. Regularly testing your environment, applying security best practices, and staying updated on the latest threats are crucial for keeping your website safe.

